UWB Scrambled Timestamp Sequence (STS): Working & Benefits
Advertisement
Introduction : As Ultra-Wideband (UWB) technology becomes the standard for precise location tracking in smartphones and automotive security, protecting the integrity of distance measurements is paramount. The Scrambled Timestamp Sequence (STS), introduced in the IEEE 802.15.4z amendment, serves as the critical security layer for these High Rate Pulse (HRP) modes. This article explores how STS utilizes cryptographic techniques to safeguard ranging data, preventing malicious actors from spoofing locations or executing relay attacks in security critical applications like keyless car entry.
What is STS?
The Scrambled Timestamp Sequence (STS) is a security feature defined in the IEEE 802.15.4z standard for UWB communication. It consists of a cryptographic, pseudo random sequence of pulses added to the physical layer of the UWB signal.
Its primary purpose is to ensure Secure Ranging. In standard UWB, devices measure distance by calculating the Time of Flight (ToF) of a signal. Without STS, an attacker could intercept and replay this signal to trick the device into thinking it is closer or farther away than it actually is. STS adds an encrypted “fingerprint” to the signal to prevent this.
The figure depicts STS positions in HRP ERDEV frame. HRP (High Rate Pulse) is a mode of operation in UWB communication that allows for higher data throughput and precision. ERDEV stands for Enhanced Ranging Device. These are devices capable of “Enhanced Ranging” features introduced in the IEEE 802.15.4z amendment.
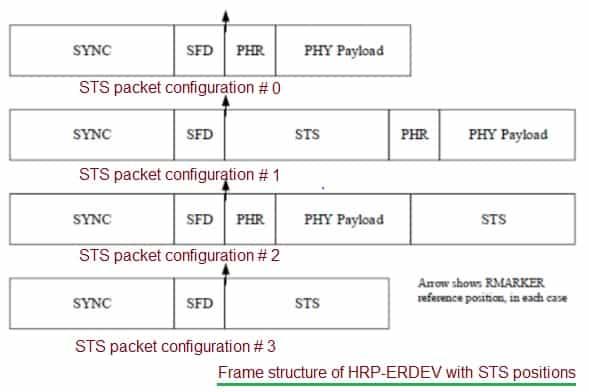
How It Works
The STS mechanism operates through a combination of cryptography and precise signal modulation.
Step 1 - Generation:
- The transmitting and receiving devices share a 128-bit secret key.
- They use an AES-128 encryption engine and a Deterministic Random Bit Generator (DRBG) to create a pseudo-random sequence of bits (0s and 1s).
Step 2 - Transmission:
- This random sequence is converted into UWB pulses using Binary Phase Shift Keying (BPSK).
- Typically, a ‘0’ bit is transmitted as a pulse with +1 polarity, and a ‘1’ bit is transmitted with -1 polarity.
Step 3 - Verification (Ranging):
- The receiving device, possessing the same secret key, generates the expected sequence locally.
- It compares the incoming signal against this expected sequence. Because the sequence is encrypted and random, an attacker cannot predict it or generate it without the key.
- If the sequences match, the receiver validates the timestamp and calculates the precise Time of Flight (ToF).
Modes of Operation
- Static STS: Uses a repeated sequence during a session.
- Dynamic STS: Uses a sequence that is never repeated during a ranging session by dynamically changing keys. This is recommended for high security applications.
Key Benefits
- Prevention of Relay Attacks: The most significant benefit of STS is stopping relay attacks which common in car theft. In a relay attack, a thief amplifies a key fob’s signal to trick the car into unlocking. Because STS relies on precise, encrypted timestamps, the car can detect if the signal was delayed by a relay device, rejecting the command.
- Data Integrity: It ensures that the timestamp data used for distance calculation has not been intercepted or altered by a third party.
- High Precision: It allows for extremely precise distance measurements and positioning, which is critical for applications like secure hands free access (e.g. unlocking a car or door automatically as you approach).
Real World Applications
STS is essential for secure location services in following applications.
- Automotive: Keyless entry systems (smart keys).
- Smartphones: Secure proximity sharing and item tracking.
- IIoT: Industrial Internet of Things applications requiring secure positioning.
Summary: STS allows receiving devices to verify the authenticity of the signal and accurately measure Time of Flight (ToF). This mechanism provides essential benefits, including high precision positioning and robust protection against data alteration, effectively neutralizing relay attacks to ensure that the measured distance between devices is both accurate and tamper proof.
Advertisement
 RF
RF




