SSL vs SSH: Key Differences Explained
Advertisement
SSL and SSH are cryptographic protocols. They are designed to secure data transmission over networks. They serve distinct purposes. Let us compare SSL vs SSH and highlights the key differences between them.
SSL
Secure Sockets Layer(SSL) is a security protocol. It establishes encrypted links between a web server and a browser. It ensures that all data transmitted remains private and integral.
- It was originally developed by Netscape.
- SSL certificates authenticate the identity of a website and enable secure connections, which are indicated by “https://” in the browser’s address bar.
- SSL has been succeeded by Transport Layer Security (TLS).
- It helps to secure login details (username, password), banking details (credit or debit card numbers, personal data) etc.
SSH
Secure Shell(SSH) is a cryptographic network protocol designed for secure remote login and other secure network services over an unsecured network.
- SSH replaces older, insecure protocols like Telnet and FTP.
- It operates as client server model.
- It typically uses port 22.
- Offers secure command line access, file transfers and tunneling.
- Used by network admins to manage servers and network infrastructures.
SSL vs SSH: A Comparison Table
| Specifications | SSL (Secure Socket Layer) | SSH (Secure Shell) |
|---|---|---|
| Full form | Secure Socket Layer | Secure Shell |
| Port number | 443 | 22 |
| Function | Used to encrypt communication between a browser and a server | Used to encrypt communication between two computers |
| Authentication | Using public key & private key pair | Using public key & private key pair OR User ID & Password Pair |
| Applications | Widely used by e-commerce, banking, healthcare, social media, government, etc. | Commonly used and adopted in the networking domain |
| Working | Operates based on certificates | Operates based on network tunnels |
Messages for SSL and SSH
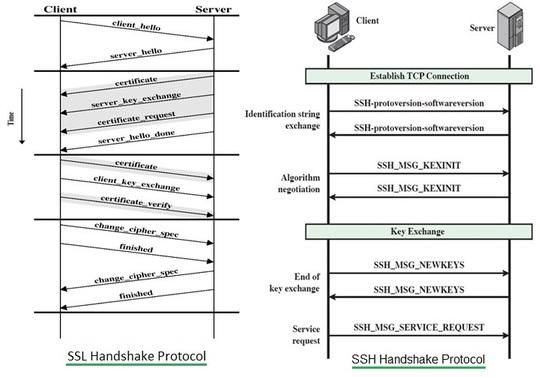
The figure depicts messages exchanged between client and server for SSL protocol and SSH protocol.
Summary
- SSL (Secure Sockets Layer) is primarily used to encrypt data between web browsers and servers, ensuring secure web communications such as online transactions and form submissions.
- In contrast, SSH (Secure Shell) is utilized for secure remote access to servers, allowing administrators to execute commands and manage systems over unsecured networks.
- While both protocols employ encryption and authentication mechanisms, their applications differ i.e. SSL/TLS secures data in transit for web based interactions, whereas SSH provides a secure channel for remote system administration.
Advertisement
 RF
RF

