CoMP and RIS: Securing 6G Distributed Wireless Networks
Advertisement
Introduction : In traditional wireless networks, security is often a conversation between two points: a single transmitter and a single receiver. However, 6G networks will be highly distributed, utilizing a dense mesh of access points, relays and smart surfaces. Let us explore how this 6G distributed architecture allows network to turn environment into defensive weapon against jammers, spoofers and eavesdroppers. There are two main technologies which make this happen in reality.
Coordinated Multipoint (CoMP)
Coordinated Multipoint (CoMP) was originally designed to help users at the edge of a cell tower’s range by allowing multiple base stations (or Transmission Points or TPs)to serve them simultaneously. In the context of 6G Physical Layer Security (PLS), CoMP evolves from a coverage tool into a security tool.
CoMP leverages Macro Diversity, meaning the signal arrives from multiple different physical locations. This spatial distribution allows the network to perform advanced signal modification that a single transmitter cannot achieve alone. Let us understand how CoMP enhances security.
- Defeating Eavesdroppers :
- Single transmitter will have limitation as it’s transmission is being caught by eavesdropper (Eva) standing in the same LOS (Line of Sight) to legitimate user (Bilal).
- CoMP uses multiple geographically separated TPs that coordinate their transmissions. They time their signal transmissions such that they are combined constructively at legitimate user’s location and combine destructively at eavesdropper’s location.
- Anti-Jamming Resilience :
- In a single-link system, a jammer only needs to block one path to cut off the user.
- In a CoMP system, the user is served by multiple TPs simultaneously. If a jammer blocks the signal from Base Station-A (i.e. TP-1), the network dynamically shifts the load to Base Station-B (i.e. TP-2). The distributed nature of the transmission makes it exponentially harder to jam the connection completely.
Reconfigurable Intelligent Surfaces (RIS)
While CoMP relies on active transmitters, Reconfigurable Intelligent Surfaces (RIS) controls the wireless channel itself. An RIS is a planar surface (like a smart mirror) covering walls or buildings, composed of hundreds of low cost passive elements that can steer, focus or scatter radio waves.
In traditional networks, the wireless channel is an uncontrollable variable (random fading, reflections). In 6G, RIS makes the channel programmable. Let us understand how RIS enables security in 6G using different approaches.
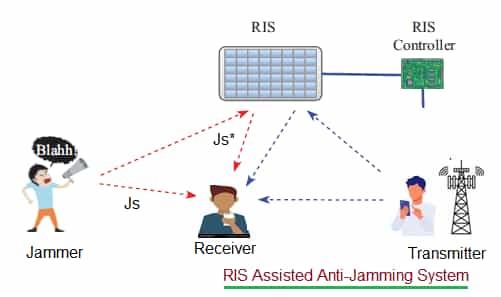
-
Smart reflection against eavesdropper : If direct line of sight between transmitter and legitimate receiver is not safe, RIS creates virtual line of sight. Moreover, RIS can be programmed to reflect “destructive interference” or “artifical noise” towards known location of eavesdropper. This creates blind spot where data can not be intercepted.
-
Cancelling jammers : RIS can be used as shield for legitimate receiver. When jammer sends jamming signal (Js), RIS can modify phase of this jamming signal. As a result, direct jamming signal (Js) and phase shifted version (Js*) of it cancel each other out. Hence clean spectrum is received by legitimate receiver.
-
Protected Zone : RIS can create protected zone around legitimate user by continuously adjusting reflection angles around authorized device.
Key Summary differences
| Feature | CoMP | RIS |
|---|---|---|
| Role | Active Transmitters: Multiple Base Stations transmit power | Passive Reflectors: A smart surface reflects existing signals without generating new power. |
| Primary Security Mechanism | Spatial Coordination: synchronizing multiple sources to confuse the attacker. | Channel Modification: Physically altering the path the wave travels to bypass the attacker. |
| Key advantages | High resilience against jamming due to multiple sources. | High energy efficiency (no active transmission) and ability to create non line of sight paths. |
Advertisement
 RF
RF

