RF Fingerprinting in 6G: Biometric Security for Devices
Advertisement
Introduction : Before arrival of 6G, devices have been identified by their MAC addresses or SIM cards. These digital identities are no longer safe as they can be cloned or spoofed by sophisticated attackers.
To provide security from such attackers, 6G networks are turning to RF (Radio Frequency) fingerprinting in which wireless devices are identified by unique biometric markers similar to human beings. Just as no two human fingerprints are exactly alike, no two wireless transmitters are identical, even if they rolled off the same assembly line. RF Fingerprinting identifies a device based on the unique, unavoidable physical imperfections in its hardware.
Biometric of Machines : Manufacturing Imperfections
RF Fingerprinting operates in the Analog Domain. It analyzes signal waveform generated by the device’s internal components. Because hardware manufacturing is never perfect, tiny variances exist in every component. These variances act as a unique signature. Following are the primary hardware components that create these fingerprints.
- Local Oscillator (LO): It generates frequency which is associated with phase noise (i.e. random fluctuations in phase) and carrier frequency offset. These drifts are unique to each LO device.
- Power Amplifier (PA) : It is used to amplify the signal. In addition, it introduces non-linear distortion when operating near maximum power. This alters the shape of the signal waveform in a predictable, unique pattern for that specific amplifier.
- I/Q Modulator : When it mixes signals (in-phase and quadrature phase), it often suffers from I/Q imbalance which are mainly gain and phase imbalances.
- Digital to Analog Converter (DAC) : The clock controlling this converter may have a unique Clock Skew or offset, affecting the timing of the transmitted signal.
How 6G utilizes and enhances RF Fingerprinting
6G further enhances rf fingerprinting to new dimensions by using following tools and techniques.
- 6G relies on Massive MIMO in which antenna arrays are soldered. This creates unique beam pattern. Authentication system relies on unique shape of the energy beam created by specific imperfections in the antenna array of the devices.
- Hardware impairments are microscopic and invisible to human eye. 6G networks use deep learning (DL) and Convolutional Neural Networks (CNNs) to detect these fingerprints.
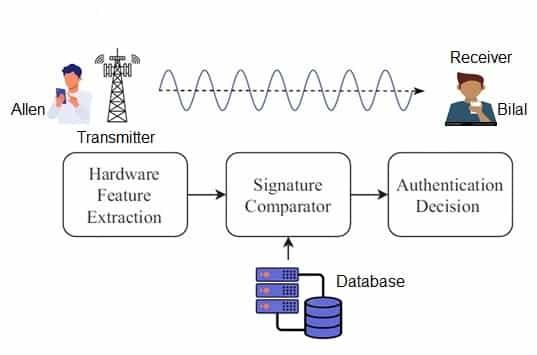
Authentication Process
Following are the steps involved in authenticating devices based on unique classifiers.
Step-1 : Signal Acquisition : The 6G Base Station receives signal from user device such as IoT sensor.
Step-2 : Feature extraction : The system isolates preamble or steady state portion of signal and strips away channel noise. It verifies hardware distortions such as I/Q imbalance or phase noise.
Step-3 : Classification (Matching) : The Base Station algorithm compares extracted distortions against database of classifiers of devices.
Step-4 : Decision :
- If it matches, the device is referred as “authenticated”.
- If does not match, the device is flagged as “spoofer”.
Summary: A hacker can steal password or clone SIM card but he/she can not physically clone microscopic manufacturing defects of specific power amplifier or oscillator. Moreover security comparison happens at the base station and do not require any energy or processing at IoT device due to passive nature of RF fingerprinting compared to traditional cryptography requiring heavy processing.
Advertisement
 RF
RF

