Traditional Cryptography vs. Physical Layer Security in 6G
Advertisement
Introduction : As we move from 5G to 6G networks, we are moving towards digital ecosystem consisting of not just smartphones, but billions of sensors, autonomous vehicles, smart implants and industrial robots.
There are limitations of traditional cryptography which is math based in next generation wireless networks which are more complex, de-centralized and heterogeneous. Physical Layer based security algorithms use laws of physics rather than complex mathematics to secure wireless communication.
How Traditional Cryptography works
As we know, traditional cryptography operates at upper layers of OSI stack and it relies on computational complexity. It uses techniques such as symmetric (e.g. AES) or asymmetric (e.g. RSA)encryption to scramble the message to be transmitted using key. Only the receiver which has the same key can de-scramble the received scrambled message to retrieve the data. The technique worked well for 4G LTE but facing hurdles in 6G wireless technology due to following reasons.
- Complex encryption algorithms consume more processing power and reduces battery life. This is fine for smartphones but will be troublesome for IoT sensors.
- Will have latency issues in 6G as traditional security implementation requires handshakes between sender and receiver and key exchanges. This will not be suitable for autonomous driving use cases in 6G networks.
What is Physical Layer Security (PLS)?
It relies on information theory and physics of wireless channel. Let us understand PLS concept with following scenario consisting of transmitter (Allen), raceiver (Bilal) and eavesdropper (Eva). Wireless signals naturally encounter noise, fading, interference and scattering as they bounce off buildings and trees when they travel from transmitter to receiver and vice versa. PLS views these impairments as unique fingerprints and not as problems.
Wireless channel between transmitter and receiver is unique to their specific locations at specific moment of time. Both transmitter and receiver use this randomness to generate secret key or hide data. An eavesdropper located even a few wavelengths away will experience different channel and will not receive secure signal correctly as transmitted between Allen and Bilal.
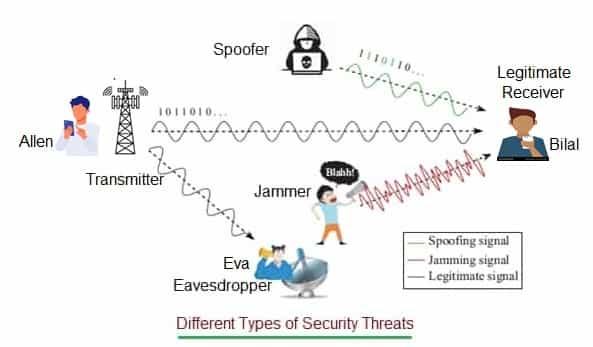
The figure depicts different types of security threats which are to be handled at physical layer to provide clear communication between transmitter (Allen) and legitimate receiver (Bilal).
Difference between traditional cryptography and physical layer security
| Feature | Traditional Cryptography | Physical Layer Security |
|---|---|---|
| Foundation | Based on Computational complexity | Based on information theory i.e. channel physics |
| Operation Layer | Upper layers (i.e. network, application) | Lowest layer of OSI stack i.e. physical layer |
| key Management | Requires complex Key Management Infrastructure (PKI). | Keys can be generated from the channel itself i.e. No exchange needed. |
| Device Requirements | High processing power and memory | Low processing power; utilizes existing radio hardware |
| Vulnerability | Vulnerable to Quantum Computer attacks | Quantum Resistant (i.e. Laws of physics cannot be hacked) |
Key benefits of PLS in 6G wireless
The PLS is very much useful in 6G wireless networks due to following advantages.
- 6G envisions massive machine type communications which uses billions of low energy devices. For these massive number of devices, it is difficult to update security keys manually nor can they handle heavy encryption algorithms. PLS offers lightweight solution without draining batteries for such IoT devices.
- PLS eliminates overhead involved in complex encryption and decryption processes required for uRLLC (Ultra Reliable Low Latency Communication) application. By securing the signal at the waveform level, the data is protected the moment it leaves the antenna, reducing delay significantly.
- PLS relies on the physical properties of the signal (i.e. noise, interference) rather than a mathematical lock, it is theoretically unbreakable by quantum computers.
- 6G networks use radio environment map which allows them to use beamforming to direct signals away from the attacker.
Summary : The future of security will see hybrid approach. We will continue to use cryptography for high level data as required in banking and finance applications and will use PLS as first line of defense. PLS will protect the network infrastructure, secure low power IoT devices and provide the random keys needed for encryption. By combining the logic of mathematics with the laws of physics, 6G networks can achieve a level of security that is not only robust but truly unbreakable.
Advertisement
 RF
RF


