6G Secret Key Generation: Extracting Keys from Thin Air
Advertisement
Introduction : As we know traditional methods such as public key infrastructure (PKI) requires heavy computation and management. Physical layer security (PLS) offers brilliant alternative of Secret Key Generation. In PLS, instead of sending key over the network, both the transmitter and receiver extract the same key from wireless channel itself.
What is Channel Reciprocity?
Let us assume that there are two persons who are communicating say Allen and Bilal and there is third person who is eavesdropper by name ‘Eva’.
As per laws of physics, radio waves travelling from Allen to Bilal and vice versa will experience almost same amount of bumps, reflections and fading. Assumption is that both side transmissions occur in very short time frame window.
As the channel is random (i.e. entropy) but identical for both the parties, it acts as shared secret source. For Eva, who is located at different spot, he experiences completely different channel and can not guess this key.
Stepwise Guide to Secret Key Generation
Following steps describe step by step guide to generate secret key.
Step-1. Channel Probing (i.e. Harvesting ) : Allen sends known pilot signals to Bilal. As the signal is received with embedded pilots, Bilal performs measurements such as RSS (Received Signal Strength) and CIR (Channel Impulse Response). Immediately, Bilal too sends pilot signals back to Allen. Allen performs the similar measurements. Due to channel reciprocity, both the measurements are roughly identical i.e. highly correlated.
Step-2. Quantization (i.e. Analog to Digital):
Both Allen and Bilal converts analog measurements (e.g. -50 dBm, -42 dBm, -60 dBm) into digital binary string of os and 1s as per common threshold (e.g. average signal strength) set. To prevent errors, both discard measurements which fall extremely close to the threshold line.
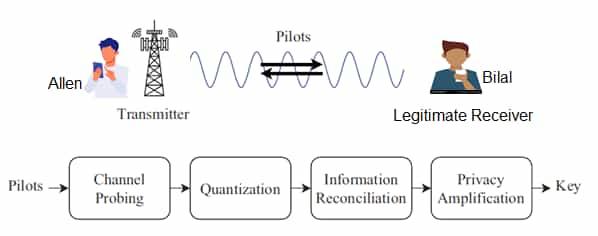
Step-3. Information Reconciliation (i.e. Error Correction):
As the hardware on both the sides are not identical, both Allen and Bilal see different noise. Due to this, binary keys estimated on both the sides are not 100% matching. To make keys identical on both the sides, both of them communicate over public channel to find and fix errors. The protocol works as follows.
- They use error correcting codes (like LDPC or Cascade protocols). For example, Allen might say, “The first block of my key has an even number of 1s.” If Bilal has an odd number, he knows there is an error in that block and uses a binary search to find and flip the wrong bit.
Step-4. Privacy Amplification (Final security) :
As mentioned, in step-3, both Allen and Bilal exchanges some hints about their key parity to fix errors. An eavesdropper listening to the public conversation might tap partial information of the key. To make final key as secure, both perform following process.
- Allen and Bilal run their keys through a Universal Hash Function which compresses the key from say 128 bit down to 100-bit key. Due to this mathematical shrinking process, Eavesdropper will have wrong key and its hacking plan will fail. Both Allen and Bilal will have completely secure final secret key.
Summary : In the above steps, we have learnt how two devices can pull a secret password out of “thin air” by analyzing the invisible radio waves connecting them.
Advertisement
 RF
RF


