WEP vs WPA vs WPA2: Wireless Security Protocol Comparison
Advertisement
This article compares WEP, WPA, and WPA2, outlining the key differences between these wireless security protocols. It covers WEP encryption/decryption, its drawbacks, and the 802.1x authentication used in WPA. We’ll also touch upon AES encryption used in the WPA2 algorithm.
Wireless security has always been a concern due to the open-air transmission medium used. Despite various security mechanisms, achieving 100% security in wireless data transmission remains challenging. WEP, WPA, and WPA2 are encryption algorithms employed in WLAN (Wireless Local Area Network) or Wi-Fi networks.
WEP Encryption and Decryption
WEP (Wired Equivalent Privacy) features include:
- Symmetric encryption: The same keys are used for both encryption and decryption.
- Key size: Uses a 40-bit key for encryption (non-standard versions may use 128-bit or 256-bit) and a 24-bit Initialization Vector (IV).
- Cipher and integrity: Employs the RC4 stream cipher for confidentiality and a 32-bit CRC polynomial for data integrity.
- XOR operation: WEP encryption and decryption use simple XOR operations.
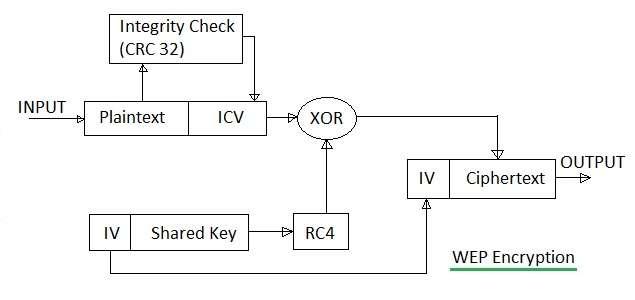
Figure 1: WEP Encryption Process Block Diagram
The WEP encryption process involves encrypting the plaintext and protecting the data from modification. The steps are:
- Encrypt the plaintext using a 64-bit key (40-bit secret key + 24-bit IV).
- RC4 uses the key as an initial seed to generate a Pseudo-Random (PN) key sequence.
- The PN key sequence is XORed with the data.
- The 4-byte IV value is added to the ciphertext before transmission.
- RC4 is applied on plain text, Integrity Check Value (ICV), and the key sequence to generate cipher text.
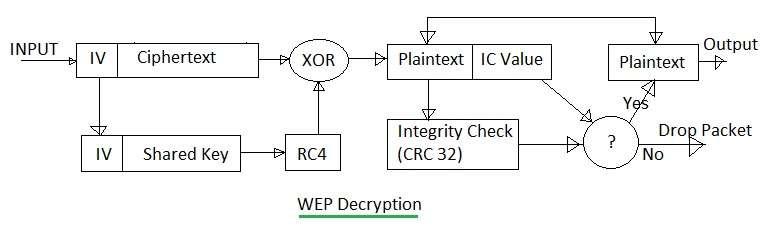
Figure 2: WEP Decryption Process Block Diagram
The WEP decryption process involves:
- Using the IV from the incoming message to generate the key sequence.
- Applying the RC4 algorithm to the ciphertext with the key sequence to produce the original plaintext and ICV.
- Determining a new ICV based on the received plaintext.
- Verifying correctness by comparing the new ICV with the decoded ICV.
- If both ICVs match, the received message is considered correct; otherwise, it’s discarded.
Drawbacks of WEP Encryption
- Shared key vulnerability: Analysis of captured traffic can reveal the shared key.
- Small key size: The 40-bit key and 24-bit IV are prone to attacks.
- One-way authentication: WEP only allows Network Interface Cards (NICs) to authenticate Access Points (APs), not vice versa.
WPA Encryption Algorithm
WPA (Wi-Fi Protected Access) addresses the drawbacks of WEP.
The main issue with WEP was that users often failed to activate it or change the default password. WPA resolves this by automatically setting keys derived from a master key and changing them regularly. Developed by the Wi-Fi Alliance, WPA comes in two types:
- WPA Enterprise: Uses a RADIUS server for user authentication.
- WPA Personal: Relies on a pre-shared key (PSK) or password entered by users, with the TKIP (Temporal Key Integrity Protocol) periodically changing the keys.
WPA features include:
- Data protection: Ensures data protection and restricts network access to authorized users.
- Interoperability: Secures and enables interoperability for all 802.11 versions (e.g., 11a/11b/11g).
- Dynamic session keys: Uses dynamic session keys via TKIP.
- Larger key sizes: TKIP uses key sizes ranging from 40 to 128 bits.
- Authentication server: Checks user credentials and grants access to authorized users only, generating and distributing keys to the client (STATION) and AP.
- 802.1x authentication: Utilizes 802.1x authentication with EAP (Extensible Authentication Protocol), which handles credential presentation in digital certificate forms.
WPA2 Encryption Algorithm
WPA2 features:
- AES encryption: Based on the AES (Advanced Encryption Standard) as defined in IEEE 802.11i.
- Developed by the Wi-Fi Alliance in association with the IEEE.
Refer to AES vs DES and AES MATLAB code for more information.
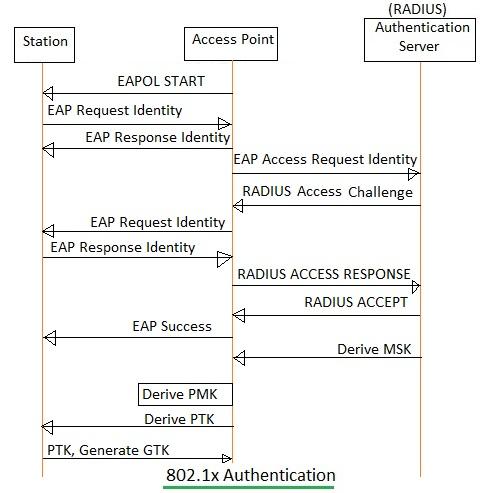
Figure 3: 802.1x authentication message flow between Station, AP, and Authentication server
IEEE 802.11i defines the Robust Secure Network (RSN) mechanism, which uses 802.1x authentication and key management protocols. The RSN authentication involves three systems:
- Wi-Fi STATION
- Wi-Fi Access Point
- Authentication Server
There are three steps involved in RSN connection establishment using WPA2:
- Request, Authentication, and Association
- 802.1x authentication
- 4-way handshake
The message exchange is shown in Figure 3.
Advertisement
 RF
RF


