5G NR Security: Key Derivation and Termination Points
Advertisement
This page provides an overview of 5G NR security basics, covering key derivation algorithms and security termination points.
Introduction:
Wireless security is paramount due to the open nature of the air interface. Consequently, various wireless technologies, including GSM, 3G, LTE, and 5G, employ a range of security algorithms to establish robust and secure wireless connections for users.
The main goal is to ensure the confidentiality and integrity of both user data and signaling information across different points within the 5G network. 5G NR offers security for the following:
- User data (DRBs)
- RRC Signaling (SRBs)
5G NR Security Key Derivation
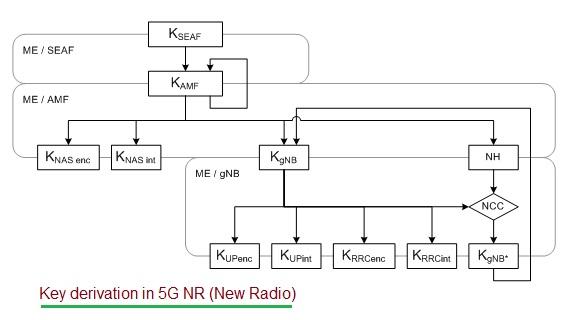
Figure 1: 5G security key derivation algorithm
Figure 1 illustrates the 5G security key derivation algorithm as defined by the 5G NR standard. The table below explains the symbols used within the algorithm.
| Keys | Description |
|---|---|
| Keys for AMF | |
| KAMF | Derived by ME |
| SEAF from KSEAF | |
| Keys for NAS signalling | |
| KNAS(int) | Derived by ME and AMF from KAMF |
| KNAS(enc) | Derived by ME and AMF from KAMF |
| Keys for gNB | |
| KgNB | Derived by ME and AMF from KAMF |
| Keys for UP traffic | KUP(enc) , KUP(int) |
| Keys for RRC Signalling | KRRC(int) , KRRC(enc) |
| Other intermediate keys | |
| NH | Derived by ME and AMF to provide forward security |
| KgNB* | Derived by ME and gNB when performing a horizontal or vertical key derivation. |
5G NR Security Key Termination Points
The following table outlines the 5G NR security termination points as described in 3GPP TS 38.300 Release 15 document.
| Security Point | Ciphering | Integrity Protection |
|---|---|---|
| NAS Signaling | AMF | AMF |
| RRC Signaling | gNB | gNB |
| User Plane Data | gNB | gNB |
References:
- 3GPP TS 38.300 V15.2.0 (June 2018), NR and NG-RAN Overall Description; Stage 2
Advertisement
 RF
RF




