NFC Security: Threats and Mitigation
Advertisement
Near Field Communication (NFC) technology is widely used in applications such as mobile payments, data sharing, and smart devices. However, with the convenience of NFC comes the challenge of ensuring secure communication. This article explores the various security measures in place to protect NFC transactions and data, including encryption techniques, authentication protocols, and how to mitigate potential threats like eavesdropping and relay attacks. By understanding NFC security, users can make informed decisions to safeguard their data in NFC-enabled systems.
As we know, wireless networks help us overcome the burden of wires used for communication in earlier days. Though it is prone to attack by intruders using various means at various network interfaces. In order to have secure wireless communication, wireless systems should have built-in security protocols at different hardware and software levels across the network architecture.
Other than the wireless network, users of the wireless network should also be cautious about certain security aspects. Before we move into NFC security aspects, let us understand NFC technology in brief. This will help in understanding the system and its operation and hence how to be cautious to overcome any security issues.
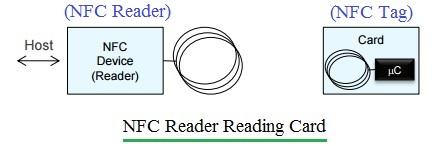
Following are the features of the NFC technology useful to understand NFC security concerns:
- It operates at a radio frequency of 13.56 MHz
- It is a short-range contactless communication system up to a distance of approximately 10 cm.
- Supports data rates of 106, 212, or 424 Kbps
- There are two devices in the NFC network: the initiator and the target. They operate in either active or passive mode. They establish a handshake before data transfer takes place. An active device will have RF fields of its own, while a passive device utilizes RF fields of the active device for operation. The initiator device (i.e., NFC Reader) will always be in active mode. The target device (i.e., NFC Tag) can function either in active mode or in passive mode.
- Manchester and modified Miller coding have been used for data modulation.
- Most common applications of NFC are payment, ticketing, and device pairing for data transfer.
Security-Related Strengths in NFC Technology
Following are the strengths of NFC technology with respect to NFC security threats:
- It encrypts the data before transmission.
- It requires synchronization or pairing between devices before communication begins.
- It is a short-range communication system, hence making it difficult to hack from a distance.
NFC Security Loopholes and Precautions to Overcome
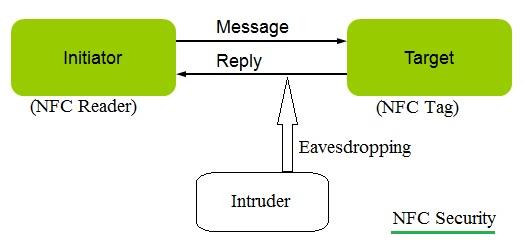
Following points highlight security loopholes and precautions to be taken care of in order to overcome them.
- As mentioned, NFC supports a range up to 10 cm, but researchers say it can have EM fields above this range which is vulnerable for possible attack when devices are in active mode. As in active mode, RF fields are stronger, especially at 106 Kbps data rate. This can be overcome by using a secure channel for communication. Moreover, use active-passive mode for communication as passive mode is harder to eavesdrop.
- The second possible attack is data modification or data corruption by transmitting undesired NFC data between two paired devices. This is more vulnerable for attack at 106 Kbps data rate. This is avoided by neglecting the EM radiation having more power at the NFC receiver. This is due to the fact that intruders’ transmitters always use more power compared to the normal transmit NFC specifications of about 10 to 20dBm. Use of a secure channel for communication is also one of the alternatives.
- Often any one person from the two paired persons will hear that someone is in the middle of the communication. By knowing the same, he/she should stop the protocol and check for disturbances. Use protocol with key agreement.
Other Useful NFC Security Tips
Following are the useful NFC security tips to overcome any security threats:
- Always use NFC-enabled certified applications for smartphones and other devices related to payments or booking.
- Check for updates from NFC device manufacturers regarding any software patches to be run. This will ensure that the NFC device being in use has the right and upgraded software. Application developers and device manufacturers update their software from time to time to incorporate security aspects.
- Keep NFC off if the device is not using the NFC facility.
Conclusion
NFC security is essential to maintaining the trust and safety of data exchanged between devices. By employing encryption, authentication, and secure transmission techniques, NFC ensures that sensitive information is protected from unauthorized access and attacks. As NFC continues to expand into more applications, understanding its security framework is key to leveraging the technology securely and effectively.
Advertisement
 RF
RF



