4G LTE Network Security: Key Hierarchy, Authentication, and Encryption
Advertisement
LTE network security is paramount for ensuring the confidentiality and integrity of data transmitted across 4G LTE networks. This guide covers the critical components of LTE security, including the key hierarchy, robust authentication mechanisms, and encryption protocols. Understanding these security layers is crucial for protecting user data, preventing unauthorized access, and defending against potential threats to the network.
As we know, security is a very important aspect of wired as well as wireless networks. It provides trust to the users/customers of the network service providers. The typical services are voice and/or data used by the users. Different systems employ security in different ways.
As we know, the LTE network consists of various system elements connected using various interfaces. The network elements are UE, eNB, MME, HSS, and AuC. The following points should be considered in order to provide LTE security:
- Nodes should be able to exchange signaling data and user data securely.
- The following vulnerable positions should be made secure in the LTE system:
- Protection at the LTE network access interfaces.
- Protection on the wireline network.
- Secured access to mobile stations by the user domain.
- Enable application domain security for applications and messages.
- Provide provisioning for the user to configure the security feature. This helps the user know whether the security is supported or not by the network service provider.
LTE Authentication and Key Agreement Mechanism
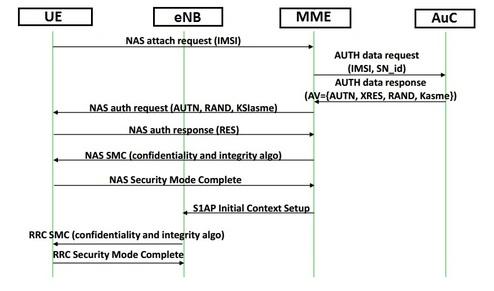
Fig.1: LTE authentication and key agreement
Fig.1 mentions the authentication and key agreement message flow between UE, eNB, MME, and AuC. As shown, authentication is initiated by the serving MME. An authentication request message is sent to the UE with authentication parameters e.g. RAND, AUTN, and KSIASME (or eKSI referred to as NAS Key Set Identifier). The KSIASME is allocated by the MME and uniquely identifies the KASME. It is stored in the UE and serving MME together with the GUTI (if available).
LTE Security Key Hierarchy
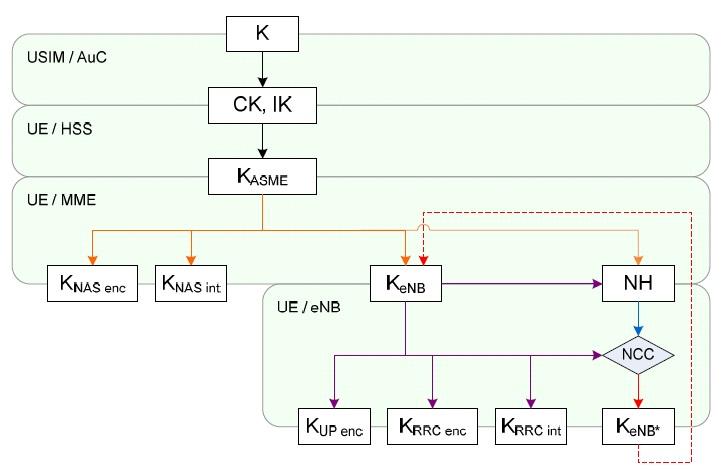
Fig.2: LTE security key hierarchy
Following Fig.2 depicts the hierarchy of security keys used in LTE EPS. The keys used for NAS and AS protection in LTE depend on the algorithms. The various LTE security keys are , , , , , , , , , , and .
| LTE Security Key | Function | Length or Size | Derived From | Basic Description |
|---|---|---|---|---|
| K | Master Base Key for GSM/UMTS/EPS | 128 | - | Secret key stored permanently in USIM and AuC |
| (CK,IK) | Cipher key and Integrity Key | 128 | ’K’ | Key Pair of Keys derived in AuC and USIM during AKA run. |
| MME (ASME) Base / Intermediate Key | 256 | CK,IK | Intermediate key derived in HSS/UE from (CK,IK) using AKA. | |
| eNB Base Key | 256 | , | Intermediate Key derived in MME/UE from when UE transits to ECM CONNECTED STATE or by UE and target eNB from during handover | |
| eNB handover transition Key | 256 | (H), NH(V) | Intermediate Key derived in source eNB and UE during handover when performing horizontal () or vertical Key(NH) derivation. Used at target eNB to derive | |
| NH | Next Hop | 256 | Intermediate key derived in MME and UE used to provide forward security and forwarded to eNB via S1-MME interface. | |
| Integrity key for NAS signaling | 256 (128 LSB) | Integrity key for protection of NAS data derived in MME/UE | ||
| Encryption Key for NAS signaling | 256 (128 LSB) | Encryption key for protection of NAS data derived in MME and UE | ||
| Encryption key for user plane (DRB) | 256 (128 LSB) | Encryption key for protection of user plane data derived in eNB and UE | ||
| Integrity key for RRC signaling(SRB) | 256 (128 LSB) | Integrity key for protection of RRC data derived in eNB and UE | ||
| Encryption key for RRC | 256 (128 LSB) | Encryption key for protection of RRC data derived in eNB and UE |
All LTE security keys (EPS) are 256 bits in length. The ciphering and integrity keys for AS and NAS algorithms use only the 128 LSB (Least Significant Bits) of the derived keys.
For more detailed information on key derivation and key hierarchy, read 3GPP 33.401 document. For KDF (Key Derivation Function) specification read 3GPP 33.220 document.
LTE Security Termination Points
Following table-2 summarizes LTE security termination points.
| Termination | Ciphering | Integrity Protection | |
|---|---|---|---|
| NAS Signaling | Required and terminated in MME entity | Required and terminated in MME entity | |
| U-plane data | Required and terminated in eNB entity | Not needed | |
| RRC Signaling (AS) | Required and terminated in eNB entity | Required and terminated in eNB entity | Required and terminated in eNB entity |
| MAC Signaling (AS) | Not needed | Not needed |
As mentioned in the table, integrity protection for U-plane is not needed and thus is not supported between UE and serving gateway OR for the transport of user plane data between eNB and Serving gateway on S1 interface.
Conclusion
In conclusion, LTE network security relies on a well-structured key hierarchy, strong authentication processes, and encryption protocols to safeguard user data and network integrity. By implementing these security measures, LTE networks can effectively mitigate risks and provide a secure communication environment. Understanding these security concepts helps ensure that LTE networks remain resilient against evolving threats.
Advertisement
 RF
RF






